After a long day at work, you come home and fire up your trusty home computer, hoping to check your email and browse the web. After what seems like ages, it finally boots up, only to immediately turn off. Frustrated, you try again; but to your dismay nothing seems to be able to resurrect it. Does this sound familiar?
Unfortunately, this is an all too common scenario. What has most likely happened is the computer has been infected with any number of viruses, trojans and spyware which hinder the performance of the computer. Some of these are able to heal themselves by connecting to the internet, while others store multiple copies on your hard disk drive in case one becomes damaged. Unfortunately, I have learned from personal experience that the fastest and only guaranteed way to restore your computer to a usable stage would be to completely reformat your hard drive and re-install the operating system, wiping all of your data. But what could be done to prevent this from happening in the first place?
For any computer that is connected to the internet, an antivirus program is an absolute must. Unfortunately, there are so many of them out there that choosing the right one becomes a daunting task. According to independent
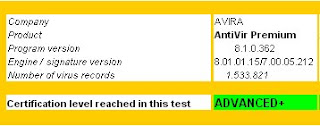
tests, a free program called Avira Antivirus detected the most viruses, malware, worms, trojans and other malware with a detection rate of 99.2% out of a set of 1,096,202 malicious programs. In terms of antiviruses, that's quite impressive.
At one time, an antivirus program was able to fully protect your personal computer. Unfortunately, spyware has been increasing in recent years, so a good antispyware program is essential. Spybot Search & Destroy searches for more than 24,000 different possible infections and is available for free
here. These programs still won't keep you safe from hackers, so a firewall is essential. Although Windows XP and Vista have
built in firewalls, a good firewall will improve the security of your computer. According to a
consumer research company, the best free firewall is Comodo Antivirus, which is available
here. All of the programs I have mentioned are free, so improving the security of your computer does not have to correlate with the draining of your wallet.








.jpg)